Details of my Master Degree, chosen Modules and Dissertation
”…A modern security professional needs to understand principles of architecture, design, management, interoperability, and evolution, and to apply them effectively in a world of rapidly-changing technologies and expectations.
The Software and Systems Security Programme at the University of Oxford teaches these principles and their application. It offers a flexible programme of short courses to those working full time in industry or in the public sector. It addresses a wide range of subjects – from service architectures to forensics, from trusted platforms to risk analysis, and from human factors to incident management. It is accessible to anyone with the right combination of previous education and practical experience.
The courses on the Programme can be used as individual programmes of professional training in specific subjects, or as credit towards a Master of Science (MSc) degree in Software and Systems Security from the University of Oxford…”
You can find a full list of the modules offered by the course HERE.
Modules and Assignments
Software - Object-Oriented Programming (OOP)
Using the Java programming language and following the “Bridge” OOP model I created a simple shipping application to send virtual packages via different postal services.
Click to expand example work
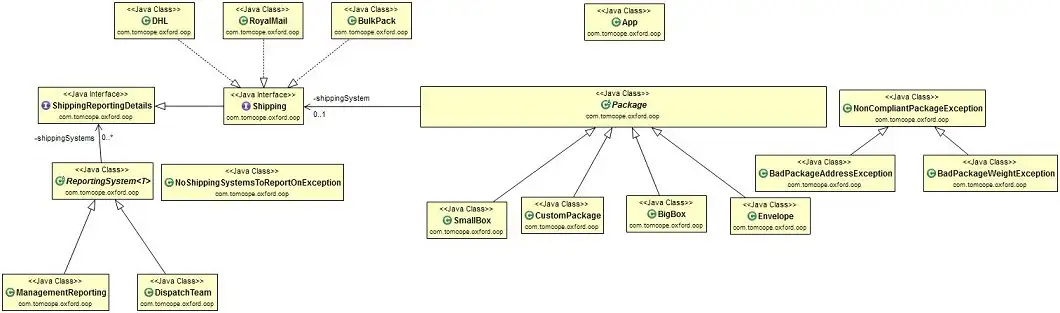
Shipping System
Oxford OOP Module
Created by Thomas Cope
Loading Application...
Main Menu:
1. Use Royal Mail
2. Use DHL
3. Use BulkPack
4. Change Item Weight
5. Check Cost, Time and Package Information
6. Dispact to Shipping Service
7. Enter Package Size to auto-select Package Type
8. Print Management Report
9. Print Dispatch Report
10. Set Package Address
q. Exit Application
-> Please Select a Option:Software - Embedded Software and Systems (ESS)
This assignment was split into two sections. The first was answering several questions such as:
- Real Time vs Safety Critical Embedded Systems
- High level vs low level languages
- FPGA with DMAs
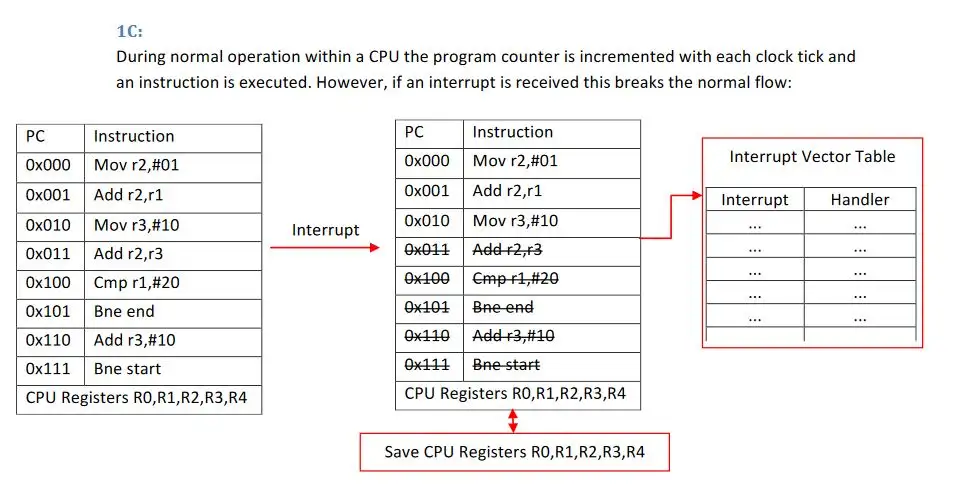
- Hardware Interrupts
- PWM
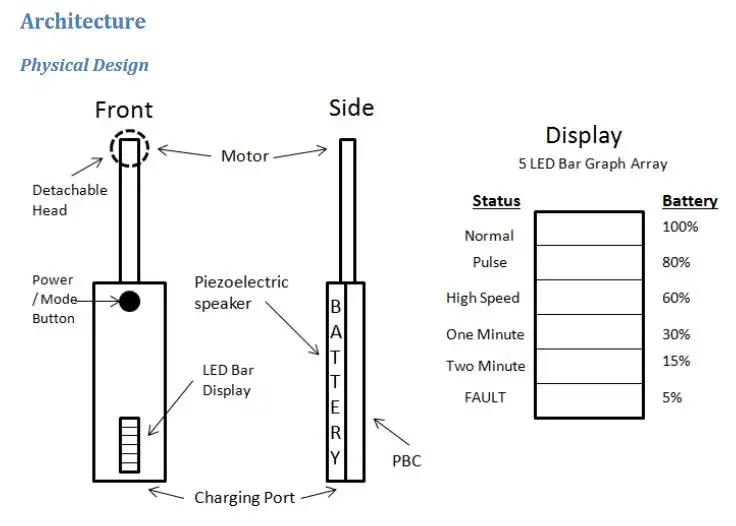
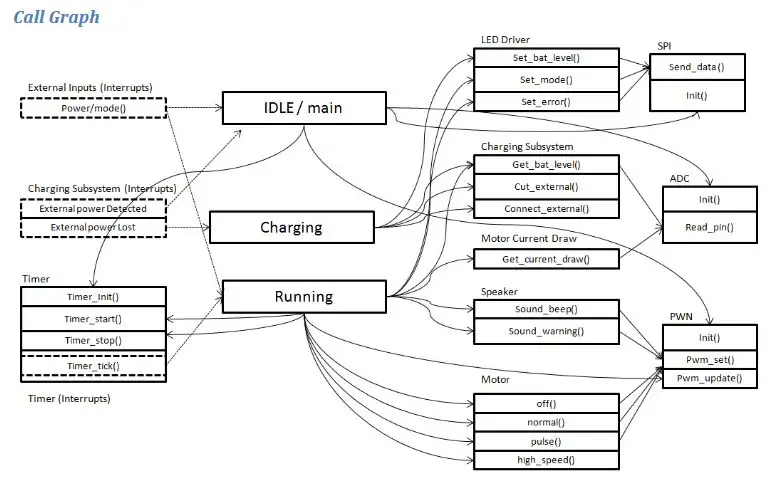
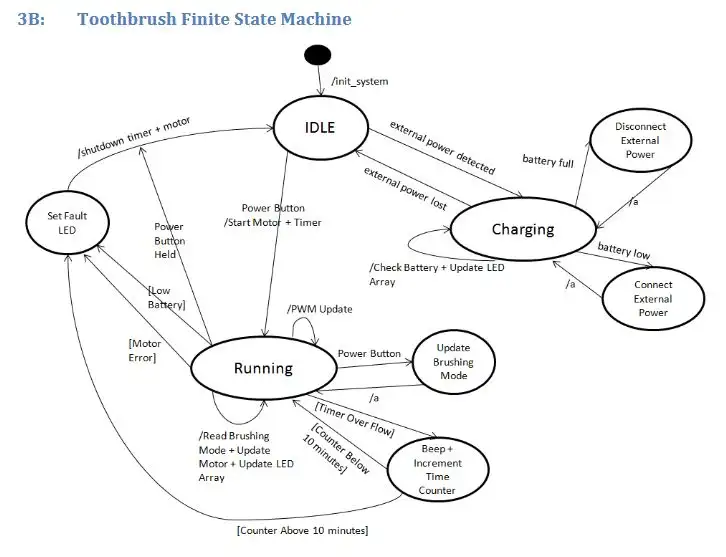
The second section used knowledge gained on the course to produce a hardware and software design for a bluetooth low energy connected electric toothbrush. This included program flow graphs and state machines. I Really enjoyed this module as it made you appreciate the complexity and engineering that goes in everyday items.
Click to expand example work
Software - Concurrent Programming (CPR)
In this assignment we had to make a “zipcar” car rental system using the Erlang programming language. The system had to be 100% tolerant to failure without losing state following the Erlang “let it crash” philosophy with the OTP runtime. The system had to allow for a unlimited number of rental locations which auto-balanced between each other to make sure no rental location was ever empty.
Click to expand example work
If you have never seen Erlang code before, this might be a bit of a shock, but below is a code snippet:
full({pickup_car}, _From, {LocID, Spaces, Occupied}) ->
{ok,[CarRef|_T]} = zc_car_register:get_cars(LocID, 1),
{reply,{zc_car_register:car_pickup(LocID, CarRef),CarRef},free,
{LocID, Spaces, Occupied-1}}; %We were full, but now can move to free.
full({return_car,_CarRef}, _From, StateData) ->
{reply, {error, full}, full, StateData}.
free({pickup_car}, _From, {LocID, Spaces, 0}) ->
%Reached empty, move to empty state.
{reply, {error, empty}, empty, {LocID, Spaces, 0}};
free({pickup_car}, _From, {LocID, Spaces, Occupied}) ->
%Get car and mark as picked up.
{ok,[CarRef|_OtherNullCar]} = zc_car_register:get_cars(LocID, 1),
{reply,{zc_car_register:car_pickup(LocID, CarRef),CarRef},free,
%Run auto_balance in case we are near full/empty.
auto_balance(LocID, Spaces, Occupied-1)};
%This function searches through all the data of each location and will compare
%against the Column which wil be either spaces, occupied or free.
%And see if they reach the required count.
search_aginst_column(LocID,AtLeastCount,Column) ->
Search = fun(X) ->
case element(2,lists:nth(Column,element(2,element(2,X))))
>= AtLeastCount of
true -> {true,element(1,X)};
false -> false
end
end,
%This runs the search against all of the pickup location data.
lists:filtermap(Search,get_other_locations_details(LocID)).
search_cars(LocID,AtLeastCount) ->
search_aginst_column(LocID,AtLeastCount,2). %Search for occupied.
search_spaces(LocID,AtLeastCount) ->
search_aginst_column(LocID,AtLeastCount,3). %Search for free.
get_other_locations_details(LocID) ->
AllLoc = lists:map(fun(X) -> element(1,X) end, lists:keydelete(LocID,1, supervisor:which_children(zc_pickup_location_sup))),
%Retrive from the suppervisor all of all of
%pickup locations and remove this one (LocID).
%For each pickup location retrive its info.
lists:filtermap(fun(X) -> {true,{X,zc_pickup_location:get_info(X)}} end, AllLoc).
auto_balance(LocID, Spaces, Spaces) -> %We are full. Need to send a Car.
attempt_send_to_free({LocID, Spaces, Spaces},search_spaces(LocID,2));
auto_balance(LocID, Spaces, 0) -> %We are empty. Need to pull a Car.
attempt_pull_to_fill({LocID, Spaces, 0},search_cars(LocID,2));
auto_balance(LocID, Spaces, Occupied) -> %No Auto Balance is needed.
{LocID, Spaces, Occupied}.
attempt_send_to_free(StateData,[]) -> %No Other Locations Avalible.
StateData;
attempt_send_to_free({LocID, Spaces, Occupied},[SendToLoc|_OtherLoc_T]) ->
%Other Locations Are Avalible, Send car to Other Location.
{ok,[ShiftCarRef|_OtherNullCar]} = zc_car_register:get_cars(LocID, 1),
zc_pickup_location:return_car(SendToLoc, ShiftCarRef),
{LocID, Spaces, Occupied-1}.
attempt_pull_to_fill(StateData,[]) -> %No Other Locations Avalible.
StateData;
The Erlang Application Monitor:
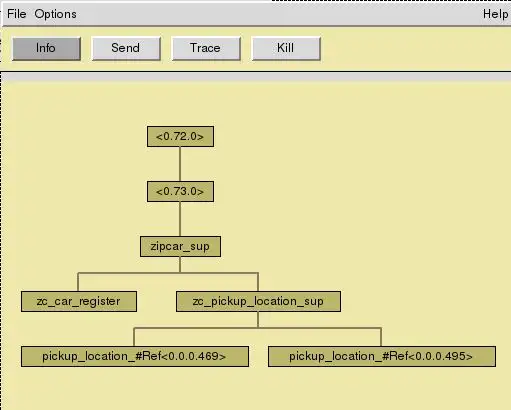
Mini Demo:

Security - Security Principles (SPR)
This module discussed the fundamentals of Security such as encryption and secure protocol design. It explained the common classes of vulnerabilities and how to avoid them.
Security - Secure Programming (SCP)
This module built upon the CPR course but focused on how vulnerabilities manifest themselves in hardware and software. The assignment was to review the “A2: Analog Malicious Hardware” paper. The paper discussed how the use of third party chip manufacturing introduces a new “fabrication time” attack vector whereby an attacker can modify a microchip to insert hardware trojans.
Security - Trusted Computing Infrastructure (TCI)
This was a extremely interesting module discussing Trusted Computing Infrastructure, trusted computing base, the TPM chip, Intel TXT and SGX. The assignment was to discuss the Capabilities of a Trusted Platform, TPM vs vTPM in the cloud and how Trusted Computing can be used to meet security and legal requirements such as GDPR.
Security - Network Security (NES)
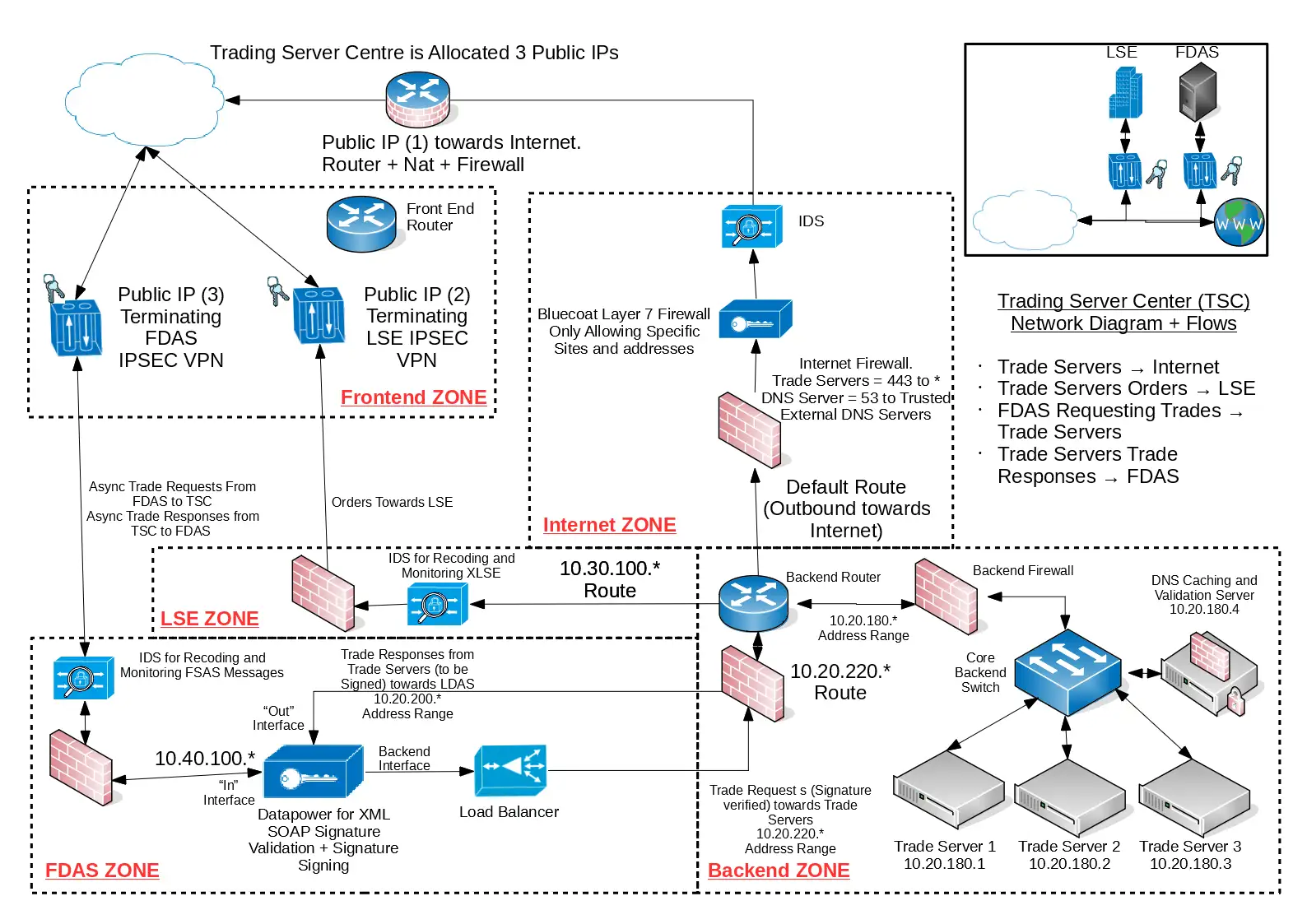
This module covered the basics of Network Security such as firewalls, network segregation, VLANs, IDS, IPS and DNS. The assignment was to produce a secure network design to meet customer requirements.
Click to expand example work
Security - Forensics (FOR)
The module discusses the various tools and techniques for performing digital forensics in a safe and secure manner. In the assignment we were given a disk image of a hard drive which we had to investigate. The image was provided in the Encase format which we verified via a md5 hash and mounted for investigation. A full detailed report was produced with supporting (extracted and recovered) evidence as if the report would be provided in a court of law (with chain of evidence). This module was very enjoyable and as part of the assignment I performed:
- An analysis of the partitions
- OS Detection
- Real, hidden and deleted user identification
- Email tracing and recovery
- Windows Encrypted File System cracking
- TrueCrypt cracking
- Microsoft Office cracking
- Email Contact tracing
- Deleted file recovery
- PGP tracking and cracking
- Image Steganography analysis
- Online account tracking and tracing
- Windows event log analysis (including external system + device detection + wifi)
- Web History recovery and analysis
Security - Understanding and Mitigating Malware (MAL)
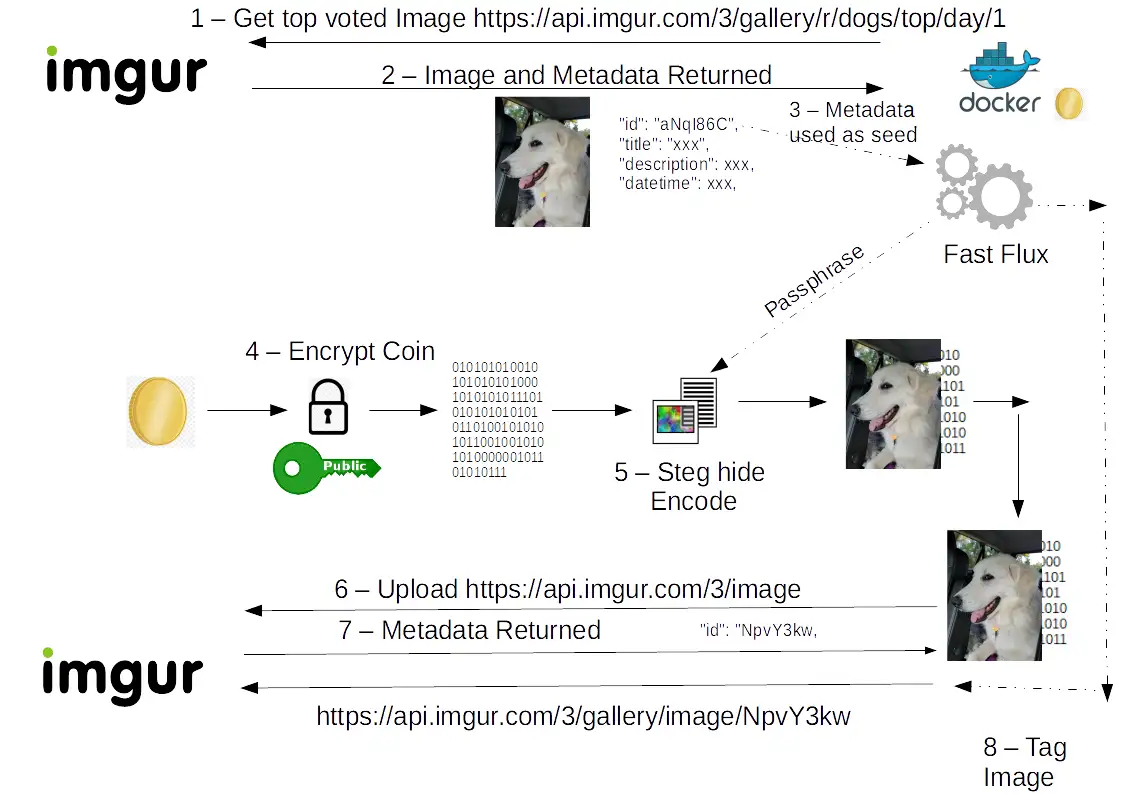
This module covered the different motives and technique’s used by Malware creators. Such as polymorphic vs metamorphic malware, fast flux systems, “money washing” and mitigation strategy’s against a targeted Malware operation (Education + Legal + Economical + Technical). For the assignment we had to design our own Malware operation and then create a mitigation strategy aginst it.
Click to expand example work
As part of the assignment I design a Command and Control system using the Imgur image sharing platform:
Security - Security in Wireless Networks (SWN)
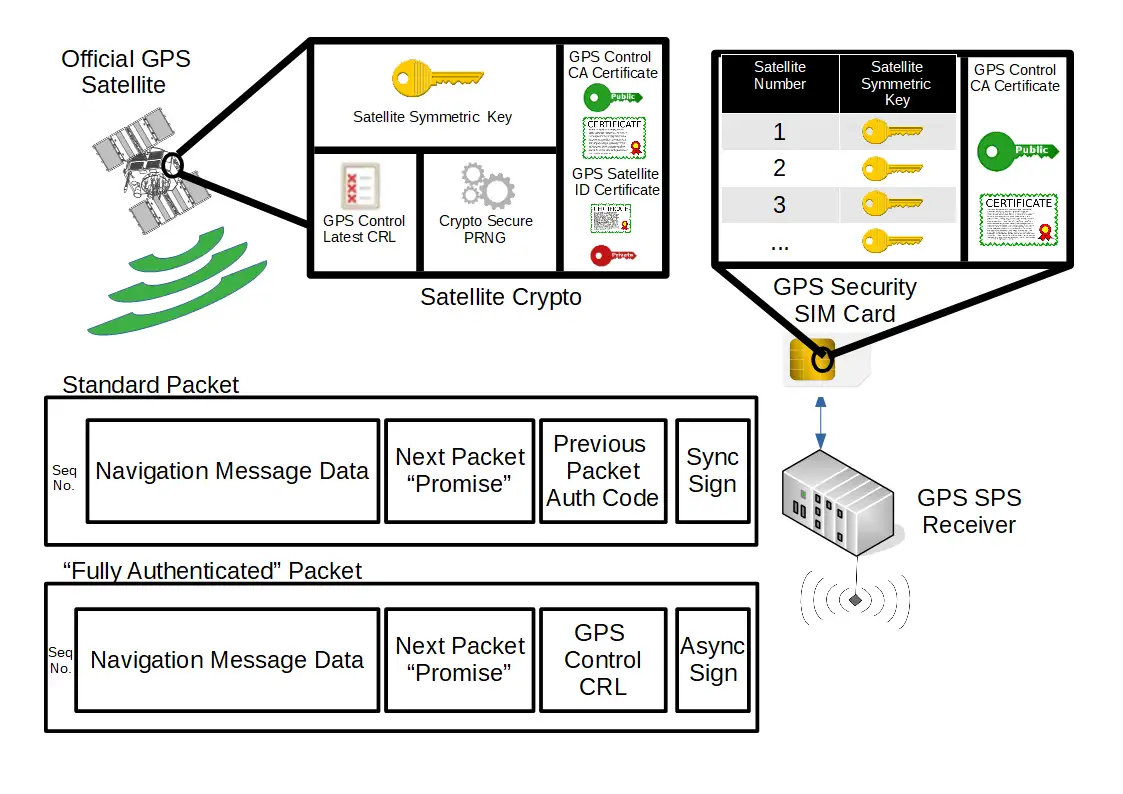
This module covered the challenges and solutions of building a secure wireless system discussing examples from: Signal propagation, PWM, Multiplexing, Jamming, Spoofing, Replay attacks, WIFI security, ZigBee, Passports, GPS, GSM, RFID and NFC.
In the assignment I discussed the (in)security of civilian and milliary GPS (L1 and L2 signals) as well as discussing countermeasures. I also created by own secure GPS solution loosely based on the TESLA protocol which I improved using a Bit commitment system combined with a SIM Card.
Click to expand example work
Dissertation
A Security Analysis of Computer Game Server Protocols
Abstract:
Computer Games were once a niche form of entertainment enjoyed by only a very small section of the demographic, but are now part of a large worldwide industry worth $36.9 billion.
What started off as a product based model where games were created and then sold, has evolved into a continuous service. In this new world instead of selling physical copies of computer games, digital game licencees are now used.
A critical aspect of the new business model is the game server protocol. If the digital game licence is the key, then the game server protocol is the lock that protects the game. The security of the protocol is of fundamental importance to players, developers and publishers. Not only does it protect the game’s revenue and prevents piracy, it also provides the means by which all players securely interact with the game.
As with every emerging market there are threat actors who may try to abuse it and take advantage. This dissertation will perform a stakeholder and threat actor analysis to better understand the threat landscape and threat model of computer game server protocols. This process will discover and analyse multiple threats such as virtual identity theft, DDOS and “game hacking” which have constantly evolved to disrupt the industry.
A game server protocol security requirement list will be created to provide a set of guidelines, which when implemented correctly will provide protection against multiple identified threats to all stakeholders. The security requirement list will be used in an in-depth protocol security analysis, testing the security of two of the most popular computer games “Minecraft” and “Counter Strike: Global Offensive”. The analysis will cover network protocols, authentication, transport systems and supporting infrastructure.
Computer games including their infrastructure and security systems have evolved greatly since their inception. These systems deviate from common standards and best practice in favour of custom implementation of everything from network code to authentication systems. Many of these systems are undocumented and have not been analysed before.
Finally, this dissertation will use the results of the in-depth protocol security analysis to propose four design recommendations to build a better more secure game server protocol. These new design recommendations can be used by future game developers to securely implement and improve their own game server protocols.