Zip Encryption Known Plain Text Attack
Posted on 05 December 2019
In this post I would like to highlight a really old flaw with the encryption used by the zip file format. This is a known text attack based on the pkcrack tool + A Paper by Dragos Barosan + The original vulnerability discovered back in 1994! By Eli Biham and Paul C. Koche
In a know plain text attack if you have the cipher text (encrypted zip file) and know some of plain text (a file inside the zip), they you can recover the key and extract all the files inside the zip!
A worked example:
I have this old zip file which I do not know the password for. I can use 7zip to open it and view its properties where we find it is encrypted using ZipCrypto and not the more common AES algorithm.
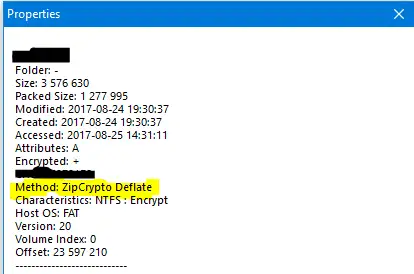
Additionally and very conventionally the zip file also contains a very old version of putty.
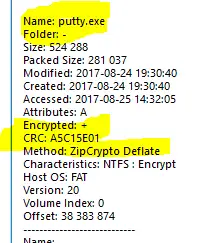
This will act as our known plain text. I don’t know exactly what version of putty this is but we can use the CRC checksum to find out! All we have todo is download lots of old versions of putty and compare their checksums with the putty inside the zip.
[tom@tomandtim zip_crack]$ 7za h
7-Zip (a) [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,8 CPUs Intel(R) Xeon(R) CPU E3-1245 V2 @ 3.40GHz (306A9),ASM,AES-NI)
Scanning
1 folder, 23 files, 55198046 bytes (53 MiB)
CRC32 Size Name
-------- ------------- ------------
lots_of_putty
53F55644 1096080 lots_of_putty/putty(20).exe
EE7F8E72 483328 lots_of_putty/putty(4).exe
49941324 524288 lots_of_putty/putty(7).exe
EDA9DDD1 829304 lots_of_putty/putty(11).exe
199F509B 495616 lots_of_putty/putty(5).exe
30B27D63 1090568 lots_of_putty/putty(16).exe
CAF59A4D 1098112 lots_of_putty/putty(18).exe
3E007457 483328 lots_of_putty/putty(3).exe
6CD97CDC 854072 lots_of_putty/putty(15).exe
F4C86100 1173000 lots_of_putty/putty(17).exe
153C4590 454656 lots_of_putty/putty(1).exe
692108A1 828400 lots_of_putty/putty(13).exe
1A573FCE 421888 lots_of_putty/putty.exe
07B01710 531368 lots_of_putty/putty(9).exe
A4C35A82 454656 lots_of_putty/putty(2).exe
2E8A61DB 524288 lots_of_putty/putty(6).exe
A5C15E01 524288 lots_of_putty/putty(8).exe <----- That looks like the one! (Release 0.66)
383949C3 1181568 lots_of_putty/putty(19).exe
561B36DA 712176 lots_of_putty/putty(12).exe
DA2AB092 1179024 lots_of_putty/putty(21).exe
59307220 774200 lots_of_putty/putty(14).exe
E377B9D8 713592 lots_of_putty/putty(10).exe
A7A58BB8 38770246 test.zip
-------- ------------- ------------
94DD3875 55198046
Folders: 1
Files: 23
Size: 55198046
CRC32 for data: 94DD3875
CRC32 for data and names: 8259971F
Everything is Ok
[tom@tomandtim zip_crack]$Now that we know the right putty version we need to zip the plain text putty using the same compression options as the encrypted version. It is very important that the two zips are as close to each other as possible. In my experience you need to use the same OS as well as the linux zip and windows zip act ever so slightly different.
Then we can use the pkcrack tool tool decrypt the encrypted zip. This can take a few minutes to run so I have sped up the gif:
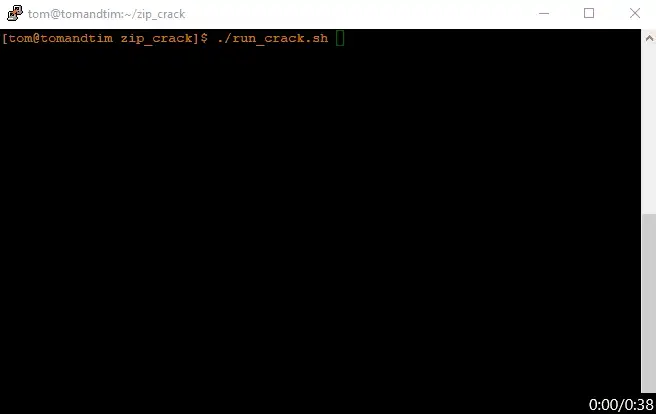
Tada!
Is this still a Vulnerability?
If you use ZipCrypto yes, yes it is. ZipCrypto is still the default encryption mode for many pieces of software such as 7zip so to avoid this issue try to use AES instead. The attacker needs 100 bytes+ of plain text to mount an attack so if you are using a common file format such as word (.docx) it is likely the word document header might be enough.